Les news relatives à la cybersécurité des installations industrielles
Retour sur la cyberattaque de Volt Typhoon qui a ciblé une compagnie d'électricité américaine
Le groupe chinois Volt Typhoon, affilié à son sous-groupe Voltzite, a ciblé le Little Electric and Water Departments (LELWD) dans le Massachusetts, aux États-Unis en 2023. Les attaquants ont exfiltré des données sensibles concernant l'infrastructure technologique opérationnelle (OT) de la centrale électrique, sans compromettre les données clients, mais l'intrusion visait à préparer d'éventuelles attaques futures. L'attaque a duré plus de 300 jours avant d'être détectée par le FBI et la société de cybersécurité Dragos. Les attaquants ont utilisé des tactiques telles que le bloc de messages serveur (SMB) et le protocole remote desktop (RDP) pour maintenir leur présence.
Medusa ransomware cible les infrastructures critiques
Le Federal Bureau of Investigation (FBI), la Cybersecurity and Infrastructure Security Agency (CISA), et le Multi-State Information Sharing and Analysis Center (MS-ISAC) ont publié un bulletin d’alerte concernant Medusa, un ransomware-as-a-service (RaaS), distinct des variantes MedusaLocker et Medusa mobile malware. Identifié en juin 2021, et à partir de février 2025, les acteurs et affiliés de Medusa ont affecté plus de 300 victimes dans différents secteurs des infrastructures critiques. Ils utilisent des techniques telles que le phishing et l'exploitation de vulnérabilités logicielles non corrigées, notamment la CVE-2024-1709 (vulnérabilité de ScreenConnect) et la CVE-2023-48788 (Fortinet EMS SQL injection).
Black Basta et Cactus : des hackers qui piègent leurs victimes avec un nouveau malware
Les groupes de ransomwares Black Basta et Cactus utilisent un nouveau malware appelé BackConnect pour garder le contrôle des machines infectées et voler des données sensibles. Ils s’appuient sur l’ingénierie sociale, en piégeant leurs victimes via Microsoft Teams ou des outils comme Quick Assist pour obtenir un accès initial. Ensuite, ils exploitent OneDriveStandaloneUpdater.exe pour charger des fichiers malveillants et renforcer leur présence sur le réseau. En 2023, Black Basta aurait extorqué 107 millions de dollars. Leur infrastructure de commande et contrôle montre des liens entre les deux groupes, suggérant une collaboration ou un partage de ressources.
-----
Nos dernières publications
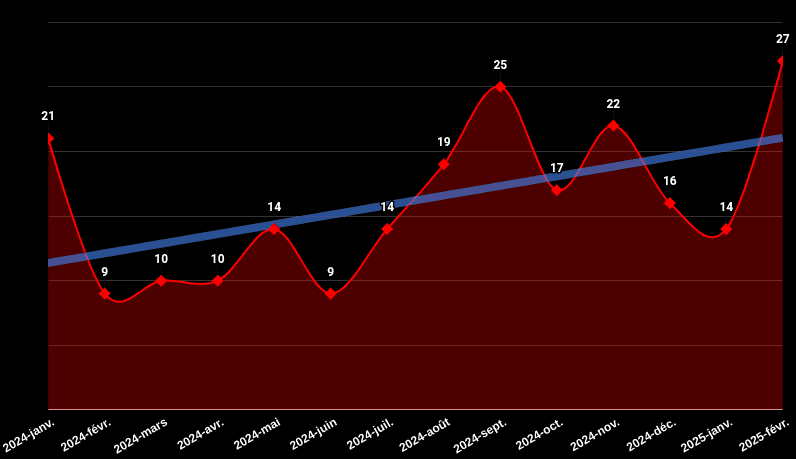
Bilan des Known Exploited Vulnerabilities du mois de février 2025
Pourquoi parlons-nous d'installation industrielle chez Fortress Cybersecurity ?
Construire son plan protection des installations industrielles contre la menace cyber : http://www.fortress-cybersecurity.fr/plan-cybersec-indus
-----
Vulnerability Corner
Liste des Known Exploited Vulnerabilities (KEV) publiés par l'agence de cybersécurité américaine CISA la semaine dernière :
CVE-2025-21590 : Juniper Junos OS Improper Isolation or Compartmentalization Vulnerability, https://supportportal.juniper.net/s/article/2025-03-Out-of-Cycle-Security-Bulletin-Junos-OS-A-local-attacker-with-shell-access-can-execute-arbitrary-code-CVE-2025-21590?language=en_US,https://nvd.nist.gov/vuln/detail/CVE-2025-21590
CVE-2025-24201 : Apple Multiple Products WebKit Out-of-Bounds Write Vulnerability, https://support.apple.com/en-us/122281,https://support.apple.com/en-us/122283,https://support.apple.com/en-us/122284,https://support.apple.com/en-us/122285,https://nvd.nist.gov/vuln/detail/CVE-2025-24201
CVE-2025-24993 : Microsoft Windows NTFS Heap-Based Buffer Overflow Vulnerability, https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-24993,https://nvd.nist.gov/vuln/detail/CVE-2025-24993
CVE-2025-24991 : Microsoft Windows NTFS Out-Of-Bounds Read Vulnerability, https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-24991,https://nvd.nist.gov/vuln/detail/CVE-2025-24991
CVE-2025-24985 : Microsoft Windows Fast FAT File System Driver Integer Overflow Vulnerability, https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-24985,https://nvd.nist.gov/vuln/detail/CVE-2025-24985
CVE-2025-24984 : Microsoft Windows NTFS Information Disclosure Vulnerability, https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-24984,https://nvd.nist.gov/vuln/detail/CVE-2025-24984
CVE-2025-24983 : Microsoft Windows Win32k Use-After-Free Vulnerability, https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-24983,https://nvd.nist.gov/vuln/detail/CVE-2025-24983
CVE-2025-26633 : Microsoft Windows Management Console (MMC) Improper Neutralization Vulnerability, https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2025-26633,https://nvd.nist.gov/vuln/detail/CVE-2025-26633
CVE-2024-13161 : Ivanti Endpoint Manager (EPM) Absolute Path Traversal Vulnerability, https://forums.ivanti.com/s/article/Security-Advisory-EPM-January-2025-for-EPM-2024-and-EPM-2022-SU6?language=en_US,https://nvd.nist.gov/vuln/detail/CVE-2024-13161
CVE-2024-13160 : Ivanti Endpoint Manager (EPM) Absolute Path Traversal Vulnerability, https://forums.ivanti.com/s/article/Security-Advisory-EPM-January-2025-for-EPM-2024-and-EPM-2022-SU6?language=en_US,https://nvd.nist.gov/vuln/detail/CVE-2024-13160
CVE-2024-13159 : Ivanti Endpoint Manager (EPM) Absolute Path Traversal Vulnerability, https://forums.ivanti.com/s/article/Security-Advisory-EPM-January-2025-for-EPM-2024-and-EPM-2022-SU6?language=en_US,https://nvd.nist.gov/vuln/detail/CVE-2024-13159
CVE-2024-57968 : Advantive VeraCore Unrestricted File Upload Vulnerability, https://advantive.my.site.com/support/s/article/VeraCore-Release-Notes-2024-4-2-1,https://nvd.nist.gov/vuln/detail/CVE-2024-57968
CVE-2025-25181 : Advantive VeraCore SQL Injection Vulnerability, https://advantive.my.site.com/support/s/article/Veracore-Release-Notes-2025-1-1-3,https://nvd.nist.gov/vuln/detail/CVE-2025-25181
Vulnérabilités de composants de systèmes industriels :
Source : ICS Advisory Project dashboard https://lookerstudio.google.com/u/0/reporting/f0d99ae7-c75b-4fdd-9951-8ecada5aee5e/page/G1klC
40 x Siemens :
Produits : SIMATIC Field PG M5, SCALANCE LPE9403 (6GK5998-3GS00-2AC2), SINEMA Remote Connect Client, Teamcenter Visualization V14.3, SiPass integrated AC5102 (ACC-G2), RUGGEDCOM RM1224 LTE(4G) EU (6GK6108-4AM00-2BA2), SIMATIC S7-1500 TM MFP - BIOS, Industrial Edge for Machine Tools (formerly known as "SINUMERIK Edge"), SINAMICS S200, Tecnomatix Plant Simulation V2302, SINEMA Remote Connect Server
5 x Critical
21 x High
10 x Medium
4 x Low
15 x Sungrow :
Produit : iSolarCloud Android App
8 x High
7 x Medium
3 x Optigo Networks :
Produit : Visual BACnet Capture Tool
1 x Critical
2 x High
2 x Philips :
Produit : Intellispace Cardiovascular (ISCV)
2 x High
Liste complète triée par CVSSv3 Score :
Vendor | Product | CVE | CVSSv3 Score | CVSSv3 Severity | EPSS | PERCENTILE | CWE |
Optigo Networks | Visual BACnet Capture Tool | CVE-2025-2080 | 9.8 | CRITICAL |
|
| CWE-288 |
Siemens | SINEMA Remote Connect Client | CVE-2024-1305 | 9.8 | CRITICAL | 0.00043 | 0.11935 | CWE-190 |
Siemens | SINEMA Remote Connect Client | CVE-2024-27903 | 9.8 | CRITICAL | 0.00067 | 0.32524 | CWE-434 |
Siemens | SINAMICS S200 | CVE-2024-56336 | 9.8 | CRITICAL | 0.00091 | 0.41287 | CWE-287 |
Siemens | Industrial Edge for Machine Tools (formerly known as "SINUMERIK Edge") | CVE-2024-42513 | 9.1 | CRITICAL | 0.00043 | 0.11935 | CWE-305 |
Siemens | SiPass integrated AC5102 (ACC-G2) | CVE-2025-27494 | 9.1 | CRITICAL | 0.00066 | 0.3187 | CWE-20 |
Siemens | SCALANCE LPE9403 (6GK5998-3GS00-2AC2) | CVE-2025-27396 | 8.8 | HIGH | 0.0005 | 0.22164 | CWE-273 |
Sungrow | iSolarCloud Android App | CVE-2024-50693 | 8.2 | HIGH | 0.00043 | 0.11935 | CWE-639 |
Sungrow | iSolarCloud Android App | CVE-2024-50689 | 8.2 | HIGH | 0.00043 | 0.11935 | CWE-639 |
Siemens | SIMATIC Field PG M5 | CVE-2024-56181 | 8.2 | HIGH | 0.00043 | 0.11935 | CWE-693 |
Siemens | SIMATIC Field PG M5 | CVE-2024-56182 | 8.2 | HIGH | 0.00043 | 0.11935 | CWE-693 |
Siemens | SiPass integrated AC5102 (ACC-G2) | CVE-2025-27493 | 8.2 | HIGH | 0.00043 | 0.11935 | CWE-20 |
Sungrow | iSolarCloud Android App | CVE-2024-50692 | 8.1 | HIGH | 0.00043 | 0.11935 | CWE-798 |
Sungrow | iSolarCloud Android App | CVE-2024-50694 | 8.1 | HIGH | 0.00043 | 0.11935 | CWE-121 |
Sungrow | iSolarCloud Android App | CVE-2024-50697 | 8.1 | HIGH | 0.00043 | 0.11935 | CWE-121 |
Sungrow | iSolarCloud Android App | CVE-2024-50695 | 8.1 | HIGH | 0.00043 | 0.11935 | CWE-121 |
Sungrow | iSolarCloud Android App | CVE-2024-50698 | 8.1 | HIGH | 0.00043 | 0.11935 | CWE-122 |
Sungrow | iSolarCloud Android App | CVE-2024-50696 | 8.1 | HIGH | 0.00043 | 0.11935 | CWE-494 |
Siemens | SINEMA Remote Connect Client | CVE-2024-27459 | 7.8 | HIGH | 0.00042 | 0.05048 | CWE-121 |
Siemens | SIMATIC S7-1500 TM MFP - BIOS | CVE-2024-41049 | 7.8 | HIGH | 0.00042 | 0.05048 | CWE-416 |
Siemens | SIMATIC S7-1500 TM MFP - BIOS | CVE-2024-42161 | 7.8 | HIGH | 0.00042 | 0.05048 | CWE-457 |
Siemens | Teamcenter Visualization V14.3 | CVE-2025-23396 | 7.8 | HIGH | 0.00053 | 0.24813 | CWE-787 |
Siemens | Teamcenter Visualization V14.3 | CVE-2025-23397 | 7.8 | HIGH | 0.00053 | 0.24813 | CWE-119 |
Siemens | Teamcenter Visualization V14.3 | CVE-2025-23398 | 7.8 | HIGH | 0.00053 | 0.24813 | CWE-119 |
Siemens | Teamcenter Visualization V14.3 | CVE-2025-23399 | 7.8 | HIGH | 0.00053 | 0.24813 | CWE-125 |
Siemens | Teamcenter Visualization V14.3 | CVE-2025-23400 | 7.8 | HIGH | 0.00053 | 0.24813 | CWE-119 |
Siemens | Teamcenter Visualization V14.3 | CVE-2025-23401 | 7.8 | HIGH | 0.00053 | 0.24813 | CWE-125 |
Siemens | Teamcenter Visualization V14.3 | CVE-2025-23402 | 7.8 | HIGH | 0.00053 | 0.24813 | CWE-416 |
Siemens | Teamcenter Visualization V14.3 | CVE-2025-27438 | 7.8 | HIGH | 0.00053 | 0.24813 | CWE-125 |
Philips | Intellispace Cardiovascular (ISCV) | CVE-2025-2230 | 7.7 | HIGH |
|
| CWE-287 |
Philips | Intellispace Cardiovascular (ISCV) | CVE-2025-2229 | 7.7 | HIGH |
|
| CWE-1391 |
Optigo Networks | Visual BACnet Capture Tool | CVE-2025-2079 | 7.5 | HIGH |
|
| CWE-547 |
Optigo Networks | Visual BACnet Capture Tool | CVE-2025-2081 | 7.5 | HIGH |
|
| CWE-547 |
Siemens | SINEMA Remote Connect Client | CVE-2024-24974 | 7.5 | HIGH | 0.00063 | 0.30612 | CWE-923 |
Siemens | Industrial Edge for Machine Tools (formerly known as "SINUMERIK Edge") | CVE-2024-42512 | 7.4 | HIGH | 0.00043 | 0.11935 | CWE-208 |
Siemens | SCALANCE LPE9403 (6GK5998-3GS00-2AC2) | CVE-2025-27392 | 7.2 | HIGH | 0.00052 | 0.23788 | CWE-78 |
Siemens | SCALANCE LPE9403 (6GK5998-3GS00-2AC2) | CVE-2025-27393 | 7.2 | HIGH | 0.00052 | 0.23788 | CWE-78 |
Siemens | SCALANCE LPE9403 (6GK5998-3GS00-2AC2) | CVE-2025-27394 | 7.2 | HIGH | 0.00052 | 0.23788 | CWE-78 |
Siemens | SCALANCE LPE9403 (6GK5998-3GS00-2AC2) | CVE-2025-27395 | 7.2 | HIGH | 0.00049 | 0.21871 | CWE-22 |
Siemens | Tecnomatix Plant Simulation V2302 | CVE-2025-25266 | 6.8 | MEDIUM | 0.00045 | 0.184 | CWE-552 |
Sungrow | iSolarCloud Android App | CVE-2024-50691 | 6.5 | MEDIUM | 0.00043 | 0.11935 | CWE-295 |
Sungrow | iSolarCloud Android App | CVE-2024-50684 | 6.5 | MEDIUM | 0.00043 | 0.11935 | CWE-327 |
Sungrow | iSolarCloud Android App | CVE-2024-50685 | 6.5 | MEDIUM | 0.00043 | 0.11935 | CWE-639 |
Sungrow | iSolarCloud Android App | CVE-2024-50690 | 6.5 | MEDIUM | 0.00043 | 0.11935 | CWE-259 |
Siemens | SINEMA Remote Connect Client | CVE-2024-28882 | 6.5 | MEDIUM | 0.00043 | 0.11935 | CWE-772 |
Siemens | SINEMA Remote Connect Server | CVE-2024-28882 | 6.5 | MEDIUM | 0.00043 | 0.11935 | CWE-772 |
Siemens | Tecnomatix Plant Simulation V2302 | CVE-2025-25267 | 6.2 | MEDIUM | 0.00052 | 0.241 | CWE-552 |
Siemens | SIMATIC S7-1500 TM MFP - BIOS | CVE-2024-41046 | 5.5 | MEDIUM | 0.00042 | 0.05048 | CWE-415 |
Siemens | SIMATIC S7-1500 TM MFP - BIOS | CVE-2024-41055 | 5.5 | MEDIUM | 0.00042 | 0.05048 | CWE-476 |
Siemens | SIMATIC S7-1500 TM MFP - BIOS | CVE-2024-42154 | 5.5 | MEDIUM | 0.00044 | 0.15769 | CWE-805 |
Siemens | SINEMA Remote Connect Server | CVE-2024-5594 | 5.4 | MEDIUM | 0.00043 | 0.11935 | CWE-117 |
Sungrow | iSolarCloud Android App | CVE-2024-50686 | 5.3 | MEDIUM | 0.00043 | 0.11935 | CWE-639 |
Sungrow | iSolarCloud Android App | CVE-2024-50687 | 5.3 | MEDIUM | 0.00043 | 0.11935 | CWE-639 |
Sungrow | iSolarCloud Android App | CVE-2024-50688 | 5.3 | MEDIUM | 0.00043 | 0.11935 | CWE-798 |
Siemens | SiPass integrated AC5102 (ACC-G2) | CVE-2024-52285 | 5.3 | MEDIUM | 0.00046 | 0.19886 | CWE-306 |
Siemens | SINEMA Remote Connect Client | CVE-2024-4877 | 4.9 | MEDIUM |
|
| CWE-420 |
Siemens | SCALANCE LPE9403 (6GK5998-3GS00-2AC2) | CVE-2025-27397 | 3.8 | LOW | 0.00046 | 0.19228 | CWE-22 |
Siemens | RUGGEDCOM RM1224 LTE(4G) EU (6GK6108-4AM00-2BA2) | CVE-2025-23384 | 3.7 | LOW | 0.00046 | 0.19886 | CWE-187 |
Siemens | SCALANCE LPE9403 (6GK5998-3GS00-2AC2) | CVE-2025-27398 | 2.7 | LOW | 0.00045 | 0.18378 | CWE-78 |
Siemens | RUGGEDCOM RM1224 LTE(4G) EU (6GK6108-4AM00-2BA2) | CVE-2025-23384 | 2.2 | LOW | 0.00046 | 0.19886 | CWE-187 |
-----
Actualité Fortress Cybersecurity
10 avril 2025 : Gestion des vulnérabilités en environnement industriel,inscription lien
15 mai 2025 : Segmentation des réseaux industriels,inscription lien
5 juin 2025 : Accès à distance et télémaintenance des actifs industriels,inscription lien

